How to Prepare for a Cybersecurity Audit (Even If You’ve Never Done One)
Let’s face it—cybersecurity audits sound intimidating.
Whether it’s your first audit or your fifth, many small and mid-sized businesses still treat them like an emergency drill rather than a proactive part of good IT hygiene.
But here’s the truth: A cybersecurity audit is not a punishment. It’s a business-critical health check—and one that could save your company from compliance fines, reputational damage, and costly breaches.
This guide will show you exactly how to prepare for a cybersecurity audit, even if you’ve never done one before. No jargon. No fear. Just actionable steps tailored for SMBs and SMEs.
What Is a Cybersecurity Audit?
A cybersecurity audit is a formal review of your business’s IT infrastructure, policies, and controls to assess how well you're protecting your data and digital assets.
It can be:
Internal – led by your IT/security team or a consultant
External – conducted by certified auditors for compliance with standards like PDPA, ISO 27001, Cyber Trust Mark, PCI-DSS, etc.
Why It Matters:
Required for certifications and government contracts
Improves cybersecurity posture
Reduces risk of fines, breaches, or insurance claim rejections
Builds trust with customers and partners
Before You Start: Key Audit Questions to Ask
Start by answering these to define the scope of your audit:
What data are we protecting? (e.g. customer, employee, financial)
What regulations or standards apply to us? (e.g. PDPA, Cybersecurity Act, PCI-DSS)
What systems and assets are in scope? (e.g. cloud, on-prem, third-party vendors)
Who will lead and support the audit?
Once you know the “what” and “why,” the “how” becomes easier to manage.
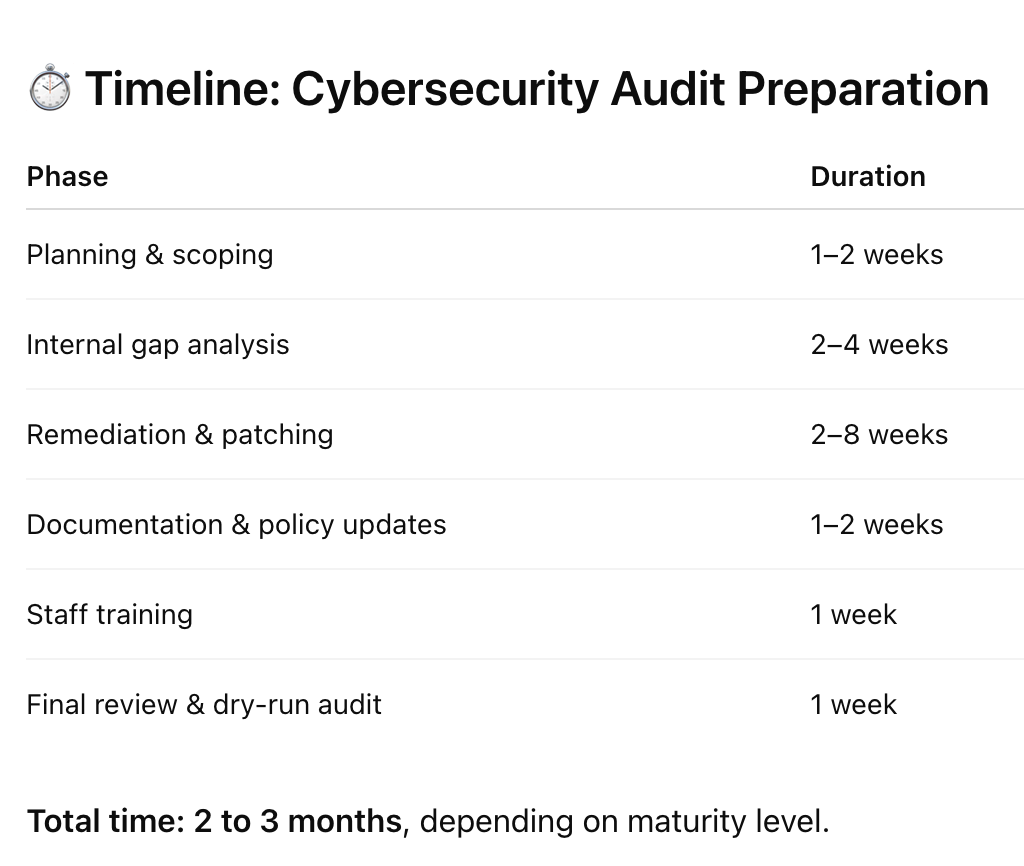
Step-by-Step: How to Prepare for a Cybersecurity Audit
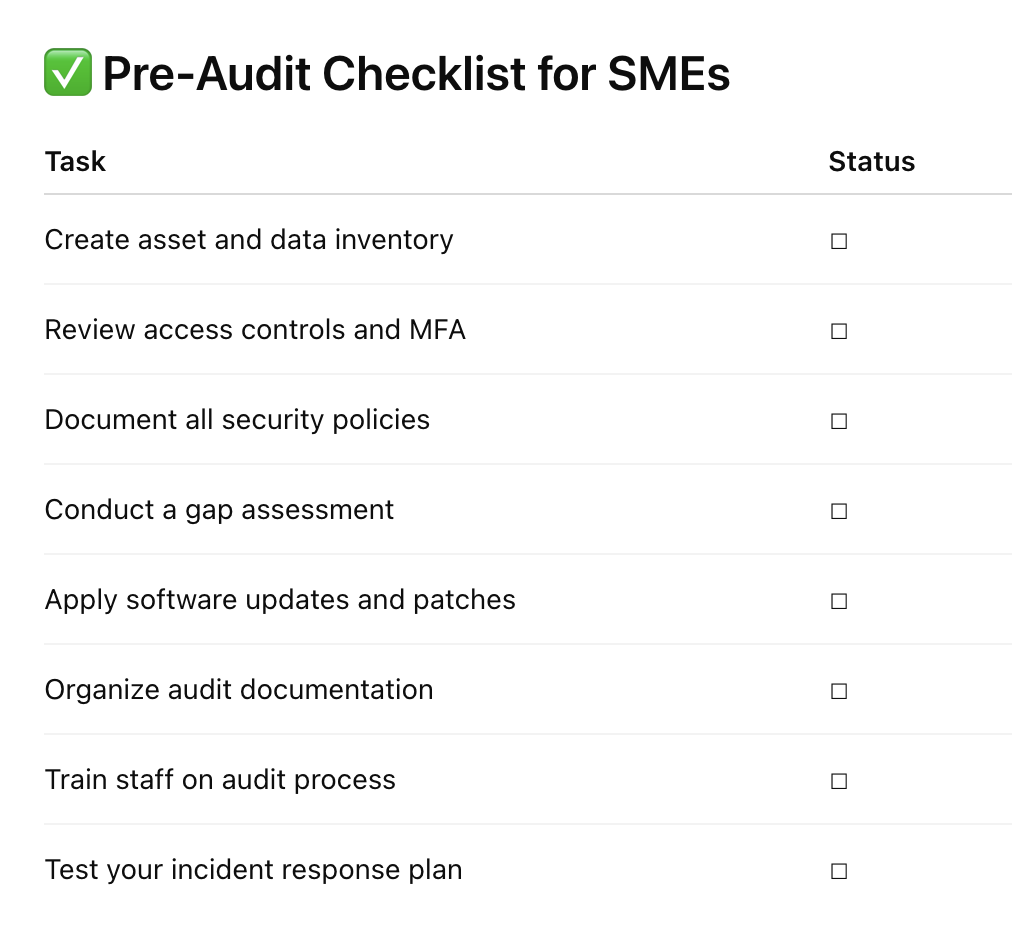
1. Inventory All Assets and Data
You can’t protect what you don’t know exists.
Create an inventory of:
Endpoints (laptops, phones, servers)
Applications (SaaS, internal apps, legacy systems)
Cloud services (AWS, Azure, Google Cloud)
Network architecture (firewalls, switches)
Sensitive data types and where they live
🎯 Pro Tip: Use tools like Lansweeper, ManageEngine, or Microsoft Intune to automate asset discovery.
2. Review Access Controls
Access management is one of the first things auditors check.
Ensure:
Role-based access controls (RBAC) are in place
MFA is enabled for all privileged accounts
User accounts are reviewed and deprovisioned regularly
Password policies follow best practices (length, complexity, expiry)
📘 Example: A fintech startup failed their first audit because terminated employees still had VPN access after 90 days—an easy fix that caused major risk.
3. Document Security Policies & Procedures
Auditors need evidence. That means written policies for:
Data protection
Backup and disaster recovery
Incident response
Acceptable use (AUP)
Mobile and BYOD policies
Vendor risk management
🎯 Don’t have these yet? Start with CSA’s Cybersecurity Toolkit for SMEs, which includes templates.
4. Run a Pre-Audit (Gap Assessment)
A gap assessment simulates an audit to find issues before the real one begins.
Assess these areas:
Compliance with relevant standards (PDPA, ISO 27001, Cyber Essentials)
Technical controls (firewalls, AV, encryption)
Administrative controls (training, awareness)
Physical controls (access to server rooms, surveillance)
Use frameworks like:
NIST Cybersecurity Framework
CSA's Cyber Essentials Self-Assessment
ISO 27001 checklist
📌 Engage a certified cybersecurity consultant if you’re unsure where to begin.
5. Patch & Update Everything
Outdated software is one of the most common audit red flags.
Ensure:
All systems are running supported versions
Patches are applied regularly (automate where possible)
Vulnerability scans are conducted monthly
🔧 Tools like Nessus, OpenVAS, or Qualys can help identify and fix vulnerabilities quickly.
6. Collect and Organize Documentation
Make your auditor’s job easy by having your documentation ready:
Network diagrams
Logs and monitoring reports (SIEM tools like Splunk or Wazuh)
Antivirus and endpoint protection status
Incident response drill reports
Data loss prevention (DLP) settings
Audit logs for privileged access
🗃️ Keep everything in a secure shared folder for easy access during the audit.
7. Train Your Team
Employees should know:
What the audit is about
What policies they must follow
How to respond to auditor questions
Run a briefing session before the audit. Make sure everyone, from IT to HR, knows their role.
📘 Stat: Companies that run internal audit prep sessions are 2x more likely to pass on the first attempt (Forrester, 2024).
8. Prepare Your Incident Response Plan (IRP)
Auditors often simulate or review past incidents.
Ensure your IRP includes:
Clear roles and contact points
Steps to detect, contain, and recover
Communication plan (internal and external)
Evidence logs
🎯 Test your IRP with tabletop exercises or mock incidents every 6–12 months.
Common Audit Pitfalls to Avoid
“We don’t need documentation—we just do it.”
“Our IT vendor handles all that, so we’re covered.”
“We’ve never had a breach, so we must be compliant.”
“Audits are only for big companies.”
Reality check: Compliance without proof is non-compliance.
Final Thoughts: Don’t Wait Until You’re Forced to Audit
Whether you’re preparing for Cyber Trust Mark, ISO 27001, or simply trying to stay PDPA-compliant, starting early makes all the difference.
Cybersecurity audits are your best opportunity to uncover vulnerabilities, tighten controls, and protect your business from digital threats.
Ready to Ace Your First Audit?
We help SMBs and growing enterprises prepare for cybersecurity audits—without the stress.
👉 Book a Free Pre-Audit Consultation
Related Posts
Top Cybersecurity Certifications for Companies in Singapore (Read now)
Understanding the Role of the Cyber Security Agency of Singapore (CSA) (Read now)
Cybersecurity Certification Roadmap: Navigating Your Path to Expertise (Read now)
Which Certificate is Best for Cybersecurity? Exploring the Top Certifications for Business Growth (Read now)
















Learn how to build a disaster recovery plan for your healthcare clinic in Singapore. Practical, PDPA-compliant guide to protect patient data and reduce downtime.