Is Your Business at Risk? 7 Early Signs Your IT Infrastructure Isn’t Compliant
Cybersecurity compliance isn't just about avoiding fines—it's about earning trust and staying in business.
In 2025, governments, partners, and even customers expect your IT infrastructure to meet regulatory and industry standards.
Yet, many SMBs and mid-sized companies don’t realize they’re non-compliant until it’s too late—resulting in data breaches, reputational damage, or failed audits.
In this blog, we’ll explore the 7 early warning signs your IT infrastructure may be non-compliant, what they really mean, and how to fix them before they become costly problems.
What Is IT Compliance—and Why It Matters in 2025
IT compliance means adhering to rules, regulations, and frameworks that govern how data is managed, stored, and protected.
These may include:
PDPA (Personal Data Protection Act) – Singapore’s data privacy law
Cybersecurity Act – For critical information infrastructure (CII)
ISO/IEC 27001 – Information security management standard
Industry-specific standards – PCI-DSS (finance), HIPAA (healthcare), etc.
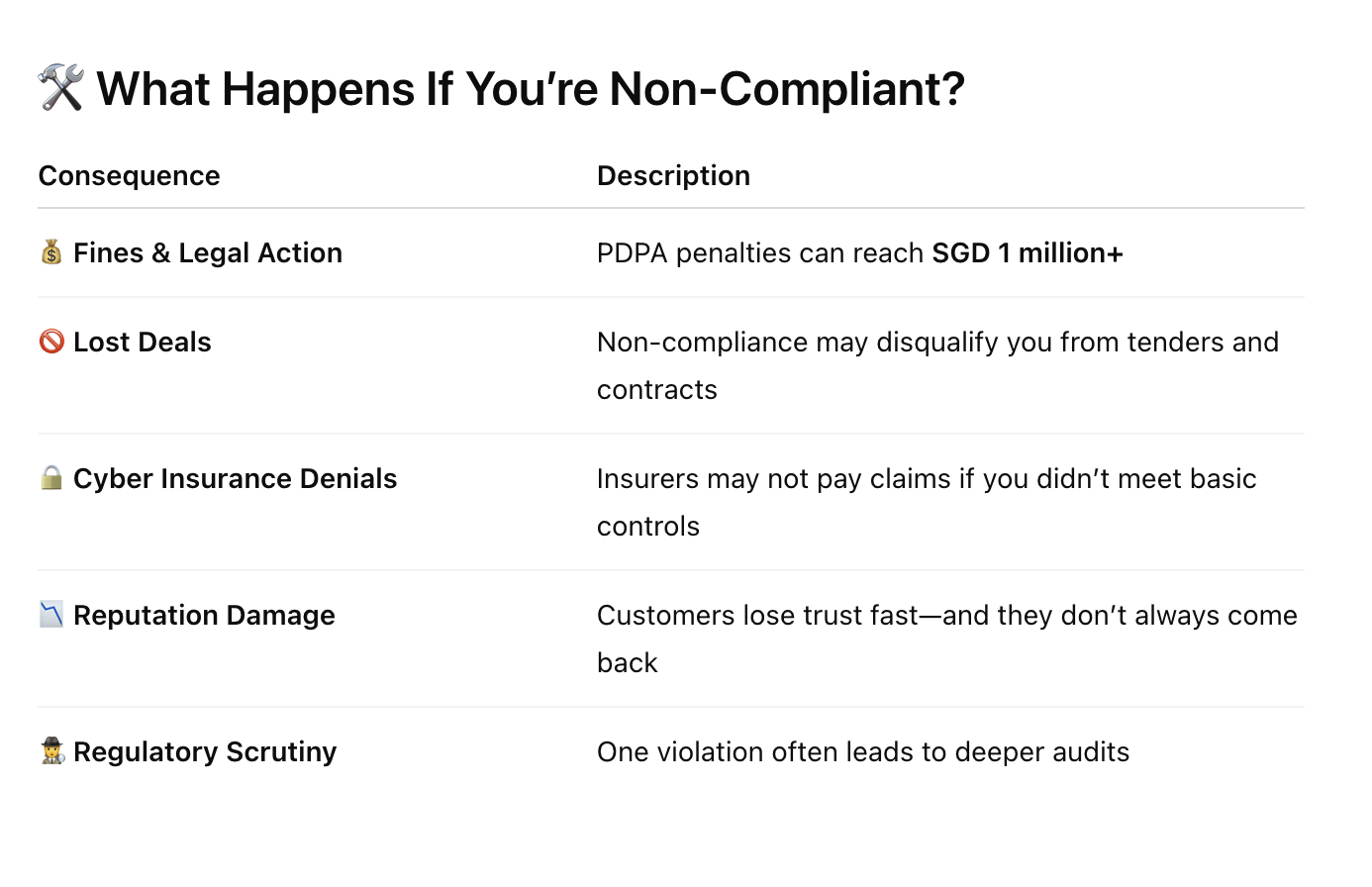
Why It’s Critical for SMBs:
Non-compliance fines can reach SGD 1 million+ under PDPA
Clients may refuse to work with non-compliant vendors
Cyber insurance claims can be denied if compliance isn’t met
SMEs eyeing growth need compliance for tenders, funding, or expansion
7 Early Signs Your IT Infrastructure Isn’t Compliant
1. No Formal Data Protection Policy
If your employees don’t know how to handle customer data, chances are your company isn’t compliant.
Red Flags:
No documented policy on data collection, usage, and retention
Inconsistent practices across departments
No DPO (Data Protection Officer) appointed
🎯 Fix it: Create a clear, written data protection policy and appoint a DPO—even a part-time or outsourced one. Refer to PDPC guidelines for templates.
2. Sensitive Data Stored Without Encryption
Storing personal or financial data in plaintext—whether in Excel files, shared folders, or legacy systems—exposes you to serious legal and reputational risk.
Red Flags:
Files on shared drives with open access
No encryption-at-rest or in-transit
External drives used without encryption
🎯 Fix it: Implement AES-256 encryption for storage and TLS 1.2+ for data in transit. Use enterprise-grade file-sharing tools like SharePoint, Dropbox Business, or Google Workspace with DLP.
3. No Access Control or Audit Trails
Can anyone in your company access your entire system? That’s a red flag for regulators and cybercriminals alike.
Red Flags:
Shared admin passwords across departments
No user role segmentation
No logging or monitoring of system access
🎯 Fix it: Use role-based access control (RBAC) and implement SIEM tools like Microsoft Sentinel, Splunk, or open-source Wazuh for tracking activities.
4. Outdated Software & Unpatched Systems
Running on old operating systems or ignoring software updates is a clear sign your infrastructure is at risk.
Red Flags:
Using Windows 7/8, outdated plugins, or end-of-life software
Delayed updates due to “business priorities”
No patch management process in place
🎯 Fix it: Set up automated patching schedules, use RMM (Remote Monitoring & Management) tools, and regularly assess vulnerabilities using scanners like Nessus or Qualys.
5. No Incident Response Plan (IRP)
When a breach happens—and it will—having no plan is as dangerous as the attack itself.
Red Flags:
No documented response playbook
No defined roles or escalation paths
No post-incident review processes
🎯 Fix it: Create an IRP that includes response teams, timelines, legal notification steps, and backups. Test it via tabletop exercises or simulated phishing attacks.
6. Employees Aren’t Trained on Cybersecurity
Human error remains the #1 cause of data breaches globally.
Red Flags:
No mandatory security awareness training
Employees reuse passwords or fall for phishing emails
No phishing simulations or refresher courses
🎯 Fix it: Run regular training with providers like KnowBe4, NTUC LearningHub, or CSA toolkits. Track improvements with simulated attacks.
📘 Case Study: A Singapore-based SME reduced phishing click rates by 82% after six months of monthly staff training.
7. You’ve Never Done a Compliance Audit
If you’ve never been through a security audit or gap assessment, chances are you're non-compliant—and simply don’t know it.
Red Flags:
No documentation for security controls
No third-party audit reports
No internal assessment or gap analysis conducted
🎯 Fix it: Schedule an internal or third-party compliance audit. Start with CSA’s Cyber Essentials Self-Assessment Toolkit.
Final Thoughts: Don’t Wait for a Breach to Get Compliant
Compliance isn’t a checkbox—it’s protection, prevention, and preparation.
If your business checks even one or two red flags on this list, now is the time to act. In today’s digital-first economy, cybersecurity is the backbone of business resilience and growth.
Ready to Secure Your IT Infrastructure?
Need a quick audit, training session, or compliance roadmap?
👉 Schedule a free 30-minute compliance consultation today
📞 Contact Us Now
Related Posts
Top Cybersecurity Certifications for Companies in Singapore (Read now)
Understanding the Role of the Cyber Security Agency of Singapore (CSA) (Read now)
Cybersecurity Certification Roadmap: Navigating Your Path to Expertise (Read now)
Which Certificate is Best for Cybersecurity? Exploring the Top Certifications for Business Growth (Read now)
















Learn how to build a disaster recovery plan for your healthcare clinic in Singapore. Practical, PDPA-compliant guide to protect patient data and reduce downtime.